There are many problems with 3D presentations, especially those with the supposedly high-gain, polarizing-friendly ‘silver screens.
(See:
23 degrees…half the light. 3D What?
Scotopic Issues with 3D,
Silver ScreensRealD and Polaroid — Possible Promise PR).
But at first glance through the breathy-for-scandle article, it seems like there is un-required hyperbole that makes one want to wait for Sony’s and RealD’s response.
This also amplifies the need for professional projectionists constantly in the projection booth, and a method for maintaining consistent quality control. If it takes a grass roots effort because of articles like this, perhaps it is OK.
But the real solution is probably to have the same “Constant Vigilance” policy for post-installation quality control as there is for security – an effort that has to come from studios, distributors, and exhibition management. In a sense, those exhibitors who signed VPF deals with studios have signed that they will make their exhibitions according to the SMPTE specification. Perhaps if the grass root effort wore t-shirts that said “48 Candelas or not at all”.
Here are a couple of shots of the lens and the projector, one with the RealD polarizers over the lenses. One suspects that this is sometimes the problem that is being talked about.


There are other shorter articles with a little more data at the links below. Sometimes the comments are the most interesting part, though a lot of them are just steam…though steam that the industry should be aware of.
Are 3D-capable theaters delivering dim 2D movies? – Digital Trends
Report: 3-D Lenses and Lazy Theaters Dim 2-D Projection by Up to 85 Percent | Movieline
Cinema chains dimming movies “up to 85%” on digital projectors – Boing Boing
Movie theaters could screw up your 2D movies by leaving the digital projector set up for 3D — Engadget
Finally, the graphic from the article: Just looking at the curve of the bulb life and the description of the Polarizing is enough to make me wonder about the truthiness of the entire article.
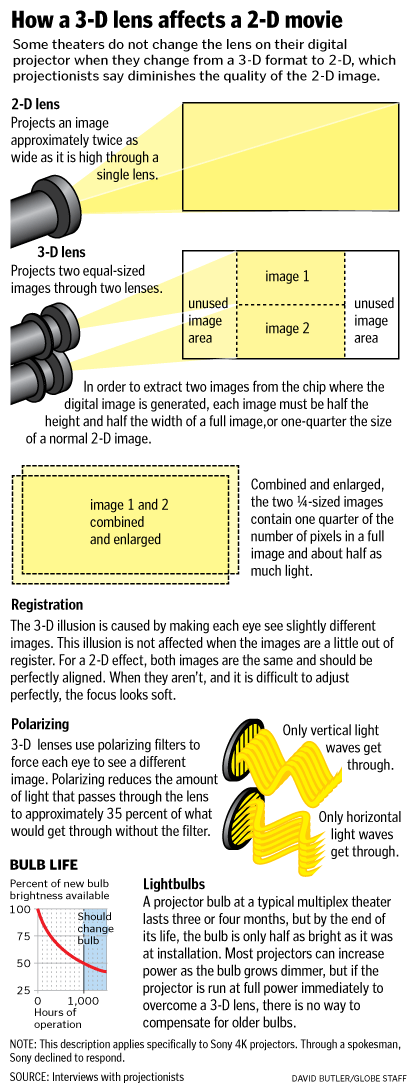
Asserted to be a Sony Press Release – 1 June 2011
The projectionist that Boston.com spoke with clearly has little to no understanding of how the systems work and is likely a manager that also works in the booth to start shows, the projectionists of yore are long gone in most cases. While the 3D lenses in the Sony are polarized, the images do not alternate, they are projected at the same time and split through a prism system in the lens, but really that’s besides the point. All of the 3D systems we have installed have been selected based on a number of variables such as screen size and auditorium length. Based on that information we can determine if the Sony projector will be able to light the screen to SMPTE spec. The SMPTE specifications on light are very clear and the DCI specification for digital equipment follows in line with that. Basically 2D digital projection should have 14 footlamberts (a measurement of reflected light) at the center of the screen, in comparison 35mm spec is 16fl of light through an open gate (meaning no film and no shutter movement) if a projector is installed to meet that spec the light output of the digital will be seen to exceed that of film. in any house where we cannot make the required light we use a bigger system, most recently these have been made by Barco.
In addition to the light levels the digital projectors are color corrected to within ±.005 of the DCI color spec. This means that when we correct with the polarizers in place on the Sony system for 2D movies that the color will be virtually identical to that seen on a DLP projector without a polarizer in the light path.
They also fail to mention some of the advantages of the way the Sony system works, such as reduced eye fatigue. DLP systems alternate images as implied in the article, they do so by electronically shifting the polarizer state for the left and right eye 3 times per frame per second. This ultimately results in the same situation you find with shutter glasses in that there is flicker that causes headaches and sometimes motion sickness, the difference is that the glasses do not actively perform this task, but close on eye while watching a 3D film ad you may see it (you may not, the system is projecting 144fps or 72 per eye, though make no mistake the content is still 24fps). The Sony system does not have this issue as it splits the 2K image across the top and bottom of the chip and then overlays them on the screen, the dual polarizers on the Sony are completely passive with not electronics involved.
To give a brief background of my knowledge base, I have been a technician for going on a decade, I have been installing digitals since the first “wide” roullout of 100 screens that Disney purchased for Chicken Little 3D. I have industry certifications through Sony, Barco and Dolby on D-Cinema equipment as well as my department’s highest level of internal certification and I am Net+ and A+ certified.
As far as why the film and digitally projected showing had such a difference, I think it’s likely one of two things, the 35mm could have been way above spec, which can happen easily due to the way the lamps are adjusted in many cases or the lamp in the digital was not adjusted properly. The biggest issue I run into is a lack of training within the theaters. I do my best to train when the systems are installed or when I am onsite for service calls, but these days so many people get rotated through the booth that should a lamp go out Friday night they just slap one in without making any of the necessary adjustments.
I’d like to know what was wrong with the management of that theater though, how do you host a premiere without making sure everything is perfect first? I myself haven’t done any due to my location within the country, but I have talked to a number of my coworkers about them and they are on site days before they happen making sure every detail is perfect. In fact many directors want to specify special color corrections for their premieres in digital or ask that sound be tweaked out of spec and so on.
I think the biggest problem digital cinema faces is that the operations departments of most chains think we can take a hands off approach to this equipment, and that is not currently the case. Proper lamp maintenance is crucial in any theater, but even more so in digital. 5-10 years from now when the laser light sources are in the field no-one will ever have need to go in the booth outside of cleaning the port glass and the maintenance calls myself and my cohorts perform.



