29 December – Krebs reports that real bad guys are breaking into Microsoft Windows computers using a newly discovered vulnerability in Internet Explorer. Now we know what a “Watering Hole Attack” is – the targeted compromise of legitimate websites thought to be of interest to or frequented by end users who belong to organizations that attackers wish to infiltrate.
Being fully upgraded does not stop this exploit~!
Attackers Target Internet Explorer Zero-Day Flaw — Krebs on Security
11 December – More Flash, eh?
Critical Updates for Flash Player, Microsoft Windows — Krebs on Security
7 November – More Mandatory Flash updates; Best explained at Adobe Ships Election Day Security Update for Flash — Krebs on Security, who warns, “Adobe urges users to grab the latest updates from its Flash Player Download Center, but that option pushes junk add-ons like McAfee VirusScan. Instead, download the appropriate version for your system from Adobe’s Flash Player Distribution page. Most users can find out what version of Flash they have installed by visiting this link.”, then goes on to explain with graphs and links the best things to do.
9 October – To find what version of Flash you have installed – click this link.
Then, Flash Player Download Center
Then, Critical Adobe Flash Player Update Nixes 25 Flaws — Krebs on Security
20 September – Solution for Explorer…kinda…Internet Explorer Users: Please Read This — Krebs on Security
18 September – Explorer Zero Day in the wild. Exploit Released for Zero-Day in Internet Explorer — Krebs on Security ONLY ONE SOLUTION: Use another browser…anything but Internet Explorer, until this is sorted out, patched and sorted out again.
5 September – Apple Users…Software Update…Java Joy…OK; Java Safety.
Apple Releases Fix for Critical Java Flaws — Krebs on Security
29 August – “New analysis of a zero-day Java exploit that surfaced last week indicates that it takes advantage of not one but two previously unknown vulnerabilities in the widely-used software. The latest figures suggest that these vulnerabilities have exposed more than a billion users to attack.”
Just get you Java change on now, and tell your friends…and read: Researchers: Java Zero-Day Leveraged Two Flaws
22 August – “For the second time in a week, Adobe has shipped a critical security update for its Flash Player software. This patch, part of a planned release, closes at least five six security holes in the widely-used browser plugin, and comes just one week after the company rushed out a fix for a flaw that attackers were already exploiting in the wild.”
Read more…everyone, that means Mac, and Windows and Linux and Android…: New Adobe Flash Player Update Fixes 6 Flaws — Krebs on Security
14 August – “…is actively being exploited to break into Windows computers…” Ain’t those just the Adobe and Microsoft words you love to hear? Active X, Flash Player, Shockwave…for Mac and PC. Clearly, not the time to be reading. Get all the computers in your domaine fixed now.
See: Critical Security Fixes from Adobe, Microsoft — Krebs on Security
6 July – A Java attack will commence on 8 July upon those who have not upgraded to the latest Java according to Krebs: New Java Exploit to Debut in BlackHole Exploit Kits — Krebs on Security
Krebs suggests that Java be turned off if unused. Apple automatically turns off Java if unused for 35 days.
Regardless, make certain that family and friends and employees are up to date with Java.
Run How do I test whether Java is working on my computer? to make certain Update 33 of Version 6 or Update 5 of Version 7 is running.
As long as you are checking, you may as well also check you vernon of Flash at:
Adobe – Flash Player
[I am doing a study on this subject. If Mac users could email me with their Java version and OS version, I would appreciate it: Editor]
22 June – Some who updated Flash recently report that there is more Firefox crashes…thus: Adobe updates Flash Player 11.3 to fix Firefox crashing problem – The H Security. The fixes are reported for Windows users, but I must say that my Mac is having weird Firefox crashes recently…like 3 or 4 in as many days.
As far as Cisco VPN, the company is full of advisories. Read H-Online for the details: Cisco closes holes in its VPN client and security appliances.
14 June – Java now, this time for Apple. Since it can take days before you computer informs you, go to Software Update now.
Krebs on Security describes it at: Apple, Oracle Ship Java Security Updates — Krebs on Security
Apple Security describes it at: About the security content of Java for OS X 2012-004 and Java for Mac OS X 10.6 Update 9
13 June – Update Windows Now, ask questions and read articles later. 26 separate security holes, three critical PLUS Microsoft XML Core Services has “Browse and Get Owned” flaws.
Microsoft Patches 26 Flaws, Warns of Zero-Day Attack — Krebs on Security
So, if you have just returned from vacation, that’s Windows, Flash changes and change your password at LinkedIn and anywhere else that you use a similar password.
8 June – Flash replacement time fixing at least 7 vulnerabilities and adding sandboxing protection to Mac users who use Firefox. Full data at Krebs:
Critical Security Fixes for Adobe Flash Player — Krebs on Security
Adobe Flash Player Download Center
Adobe Flash Removal tool
Meanwhile, if you haven’t been following the embarrassing news from LinkedIn, eHarmony and Last.fm, it is time to change your passwords to any and all of them, and ANY ACCOUNT THAT YOU HAVE THAT USES THE SAME OR SIMILAR PASSWORD. You can read about this, or you can just get started and come up with a new password phrase and change every password that you have.
Password leaks bigger than first thought
Millions of Last.fm passwords leaked eHarmony admits to leaking 1.5 million passwords
Comment: LinkedIn and its password problems
And, just because Microsoft and Flame should own each other forever:
Flame – oversights and expertise made for Windows Update worst case scenario
Windows Update compromised
5 June – Flame and Windows; at one time it seemed like Flame was going to be a real lesson, and it would be a non-event. Just a virus/trojan package that has been around for a few years, hitting ‘those guys’ in the middle-east somewhere. Now it turns out that hundreds of thousands of people are affected and have been for a long while, and that it was signed by a Microsoft SSL Certificate and the only thing certain is that there are more surprises ahead.
Then today Microsoft says they have a solution, download an update today. Oops, another news story says that the hackers have performed a “man in the middle attack” that allows them to infiltrate your computer when you think that you are getting a real Microsoft Software Update.
The answer is that you must have your employees upgrade their Windows software. Read the stories yourself:
Microsoft Update and The Nightmare Scenario – F-Secure Weblog : News from the Lab
Flame alleged to have infected systems via Windows Update
Flame worm was signed by forged Microsoft certificate
‘Flame’ Malware Prompts Microsoft Patch — Krebs on Security
Don’t believe this Update notice…or at least don’t let anyone click on it…upgrade with the standard upgrade pull down on the Start menu.
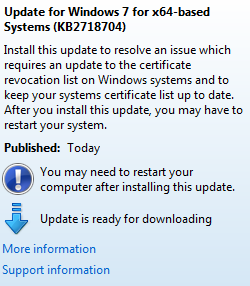
9 May – “I just went through several days of hell after Microsoft’s truly massive Patch Tuesday updates trying to fix my Adobe PremierePro CS5 edit system, only to discover that Nvidia released an update to ALL the Quadro cards on May 4 that is required in order for ActiveX to work properly after the Patch Tuesday events.” Robin McCain reports at Cutter-Talk. “This may or may not affect Mac owners who use Quadro cards for editing, but it is worth checking out if you suddenly have problems…”
Meeanwhile, Apple pushes on with several security fixes in a 350MB 10.7.4 upgrade…and a similar upgrade for 10.6 users. Use the Software Update pull down. Here is the Security Issue:
About the security content of OS X Lion v10.7.4 and Security Update 2012-002
15 April – Use the standard Apple Software Update pulldown now because: “This Java security update removes the most common variants of the Flashback malware.
This update also configures the Java web plug-in to disable the automatic execution of Java applets. Users may re-enable automatic execution of Java applets using the Java Preferences application. If the Java web plug-in detects that no applets have been run for an extended period of time it will again disable Java applets.” About Java for OS X Lion 2012-003
10 April – “What makes this bulletin stand out is that Microsoft is aware of attacks in the wild against it and it affects an unsually wide-range of Microsoft products, including Office 2003 through 2010 on Windows, SQL Server 2000 through 2008 R2, BizTalk Server 2002, Commerce Server 2002 through 2009 R2, Visual FoxPro 8 and Visual Basic 6 Runtime,” Kandek said. “Attackers have been embedding the exploit for the underlying vulnerability (CVE-2012-0158) into an RTF document and enticing the target into opening the file, most commonly by attaching it to an e-mail. Another possible vector is through web browsing, but the component can potentially be attacked through any of the mentioned applications.”
Other notable fixes from Microsoft this month include a .NET update, and a patch for at least five Internet Explorer flaws. Patches are available for all supported versions of Windows, and available through Windows Update.
Adobe’s updates fix critical problems in Acrobat and Reader on all supported platforms, including Windows, Mac OS X, and Linux.”
Read the whole Krebs On Security article: Adobe, Microsoft Issue Critical Updates
3 April – Java Update for Mac…jeesh…holiday presents for everyone. Seeing as how there are active threats against Java, just run the Mac Updater.
27 March – New Java Attack Rolled into Exploit Packs is how Krebs on Security is describing the latest security hole in your universe’s wa. Read the details and kill any unnecessary Java tools for now.
13 March – Remote Desktop Protocol from Microsoft…ever turned it on? Sitting there on any of your systems? RDP Flaws Lead Microsoft’s March Patch Batch — Krebs on Security
Don’t read anymore…just make certain that you and all the people who ever send you mail and all their friends who send them mail are updated. Good luck.
16 Feb – The exploit seems to affect IE users on Windows at this time, but Adobe is telling everyone to go to the Adobe Flash Player Download Center and get the latest inoculation. Krebs says (Flash Player Update Nixes Zero-Day Flaw — Krebs on Security):
“…although if you’re not careful to untick the check box next to whatever “optional” goodies Adobe tries to bundle with Flash Player (the most common is McAfee Security Scan Plus) you could end up with more than you wanted.”
14 Feb – Patch Tuesday…but don’t update Silverlight…jeesh. For those keeping score, with 21 security holes on 9 updates for MS and 9 vulnerabilities for Shockwave, put aside 30 minutes per machine today. Come back and do the silverlight/.NET update last, by itself. Here’s the scoop from Krebs: Critical Fixes from Microsoft, Adobe — Krebs on Security.
Mac users: You will probably need the Silverlight upgrade as well if you use sites such as Netflix and poke here to check your Shockwave.
13 Fab – More Firefox urgent security upgrade news. Get 10.0.01 now. Versions before the recently release 10.0 do not have this problem, but had other security issues. Use after Free means what it sounds like. You set your browser free because you love it so much, and it gets abused.
3 February – Tibetan Restaurant? If your Windows browser goes to a Tibetan restaurant on its own, suspect a very clever Trojan, and suspect that code is being dumped onto your computer. Most Trojans get caught because they start doing something when loaded. This trojan waits, then innocently gives a command for this website.
As this H-Online article states: “This example once again shows how important it is to install a virus scanner with a behaviour monitor.”
Trojan downloader is a problem for virus scanners – The H Security: News and Features
2 February 2012 – Non-Lion OSX users should not delay with the current security update, though none of the flaws are known to be in the wild. About the security content of OS X Lion v10.7.3 and Security Update 2012-001
27 Jan – Microsoft Again! Update against what is being termed a “browse-and-get-owned flaw for Windows XP, Windows Vista, Windows Server 2003 and 2008 users, meaning these folks can infect their machines merely by browsing to a hacked or malicious site hosting a specially crafted media file. If you run Windows and have delayed installing this month’s updates, consider taking care of that now by visiting Windows Update.” This is from Krebs, who also point to a new and dangerous PC Anywhere flaw that PC Anywhere says, “REPAIR OR REMOVE.”
Go to: Warnings About Windows Exploit, pcAnywhere — Krebs on Security
10 January – If you use Acrobat, Adobe Reader or Windows, it’s time to patch…Oy! According to Krebs on Security, Adobe, Microsoft Issue Critical Security Fixes there are enough reasons to drop everything and update now. I mean, critical is blasé and “seven security bulletins addressing at least eight vulnerabilities” is barely worth a comment.
29 Dec – Security researchers have released new tools that can bypass the encryption used to protect many types of wireless routers. Read the whole article at: New Tools Bypass Wireless Router Security — Krebs on Security
21-update on 27 Dec – Update Firefox now…MS, run Updates again, but the horror of another hole is exposed…first blamed on Apple’s Safari but as it turns out it is a MS flaw in Windows 7, potentially with all browsers…first thought not a problem on 32 bit systems but now seen to be 7-wide…no exploits seen now…but stay aware…and teach others in your circle.
Microsoft confirms Windows vulnerability – The H Security: News and Features
Critical holes in Firefox, Thunderbird and SeaMonkey – The H Security: News and Features
14 December – Critical Microsoft Updates. Force the updates now, then read why:
Security Updates for Microsoft Windows, Java — Krebs on Security
13 pre-Christmas patches from Microsoft – The H Security: News and Features
30 Nov – Critical Ultimate Critical – Update Java Now everywhere. All systems on all platforms are vulnerable to active exploits. Upgrade Now.
Read Public Java Exploit Amps Up Threat Level — Krebs on Security
Do nothing before doing this, and tell all your friends.
12 November – Critical Flash Update Plugs 12 Security Holes
13 October – Apple Safari’s turn – urgent. Upgrade now! This means you and everyone you know.
11 October – Microsoft Updates Galore. Don’t delay. Including iTunes for Microsoft. See: Critical Security Updates from Microsoft, Apple — Krebs on Security
3 October –Android seriously exposes yourself: Backdoor in HTC Android smartphones – Update
Firefox 7 also seems mandatory, but 7.1 is as well: Security Advisories for Firefox shows 7 critical vulnerabilities in 7 that need repairing with the latest, but earlier issues on 7 show that upgrading from 6 was important as well. Mozilla details security fixes in Firefox and Thunderbird updates
28 Sept – Skype for iOS repaired, PDF Pretense exposed
Force an update on your iOS Skype, as they have repaired a flaw that could expose your contact list, among other things.
Last week, Mac Trojan hunters found what appears to be a proof-of-concept use of a malware program for the Mac hidden inside a PDF. Open the PDF and the other program opens in the background. Today Apple has added that to their super list of Super Don’t Open XProtect malware signature list. Great, if you are using 10.5 or above.
But this might be a perfect time to bring up the question, “Why is anyone in need of security using a PDF file that isn’t secure. The only secure PDF file is a PDF/A file, also known as standards called ISO 19005-1 and ISO 15930-3 – that’s PDF/A-1 and PDF/X-3. It appears that we are entering the age of darkness.
21 Sept – If Vegas had a betting line on Adobe Flash being secure, you couldn’t get any takers. Here we are again. Read Krebs, or just force an update…ALL Operating Systems. Flash Player Update Fixes Critical Flaws — Krebs on Security
14 Sept – “correct critical vulnerabilities in the programs that could be exploited by attackers just by convincing users to open a booby-trapped file.” For 3 points, is that Adobe generally, Adobe Reader or Adobe Acrobat? Choose any three.
Don’t forget Microsoft: Excel, Office, Windows Server and SharePoint upgrades for security holes.
Get those patches now. So sayeth: Adobe, Windows Security Patches — Krebs on Security
30 Aug – SSL Cert Violation Repaired! – Mandatory Firefox and Chrome Updates – False SSL certificate violation repaired. See stories at: Updated Chrome and Firefox for fraudulent Google certificate available – The H Security: News and Features
and
Fake Google certificate is the result of a hack – The H Security
Or, don’t read the articles and just do the updates now…Madatory, as in Danger Will Robinson…now now now
10 Aug – Updates for Adobe Flash, Shockwave, AIR are mandatory. Read the Krebs on Security link for details, and do it now.
28 July – Force an update of iOS 4.3.5 now. There is a real SSL security hole that is fixed with this version.
12 July – “Zitmo (on the Android) is designed to intercept the one-time passcodes that banks send to mobile users as an added security feature. It masquerades as a component of Rapport, a banking activation application from Trusteer. Once installed, the malware lies in wait for incoming text messages, and forwards them to a remote Web server.” Read the rest of this horror story and keep your dcinema keys off of any Android tool. ZeuS Trojan for Google Android Spotted — Krebs on Security
15 June – If you repaired your Adobe Reader or Flash last week, cut out some time to re-do it today. (The only pain is closing all those 100 browser windows you have open.)
MS has 34 fixes available, including some for Mac Office users.
Since both the Adobe and the Microsoft issues address active malware in the wild, do not hesitate to protect your systems…again.
Krebs on Security has two excellent articles: Microsoft Patches Fix 34 Security Flaws AND Adobe Ships Security Patches, Auto-Update Feature
6 Jun – Adobe Flash is finally repaired. Any computer that touches a USB stick that touches a DCinema server must immediately update, at Adobe Update Site. This affects all OS, including Mac and Linux, so update party everyone.
Google Chrome will auto-update but not run the code until a reboot is done. So, do so.
The Zero Day problem that Flash was a magnet for is not gone into in much detail on the Adobe site. Security by Obscurity – bad news for us all.
3 June – Malware Mutates should be the headline. For extra protection see the following article (with pictures and arrows!): Mac Defender mutates past security update – The H Security: News and Features
31 May – Apple released an OS upgrade to attack the MacDefender malware. It is 2.1 Megs. Get the Upgrade process started now while you read the details at Krebs on Security: Apple Update Targets Mac Malware — Krebs on Security.
Your computer will eventually do this, but it cannot be relied upon to make this update immediately. Force a “Software Update” by clicking on the top left Apple icon and click on the Software Update link.
KNOW AND TELL OTHERS THIS ! ! ! – This particular upgrade is not ready yet for OS 10.5 or below. Also, it does not protect against infections through USB drives, BitTorrent downloads and other similar methods of penetration. This is not going to be the last that Mac users hear of this.
Apple releases update to protect against MacDefender | Naked Security says:
My impressions? A good reaction from Apple in a short amount of time. They are making the best of what is available in the OS X platform at this time. Unfortunately it falls short in many respects.
The biggest problem is the lack of an on-access scanning component. While LSQuarantine works to protect against downloads in most browsers, it doesn’t prevent infections through USB drives, BitTorrent downloads and other applications.
Daily updates are a good start, but it remains to be seen how frequently the criminals may release new variants. If they start moving in a polymorphic direction similar to the one the Windows malware writers have gone, XProtect will have issues.
Of course this update only applies to OS X 10.6 “Snow Leopard,” so older Mac users are left unprotected.
OS X 10.6 users should apply this update as soon as possible, and I recommend installing a more fully featured anti-virus solution like our freeSophos Anti-Virus for Mac Home Edition. It’s totally free; we don’t even ask you for your name or email.
26 May – Mac malware just got serious. Definitely go to Safari Preferences and under General uncheck “Open ‘safe’ files after downloading”. But that may not help if a varient of the malware named MacDefender is able to load its two files – somehow they are able to load without a password, according to Intego. Mac Defender variant doesn’t require admin password – The H Security
— And you PC users shouldn’t be gloating. A zero-day cookie monster can do whatever it wants: Internet Explorer: cookie theft made easy – The H Security.
25 May – Mac Malware, “MacDefender, MacProtector and MacSecurity” are attacked by Apple. The following Knowledgebase Document tells how to get rid of the phishing software if you have been hit, and news is that there is an OS update coming that will remove all known variants of the bad code.
How to avoid or remove Mac Defender malware
24 May – LinkedIn security needs improvement according to H-Security: LinkedIn is careless with access cookies – The H Security: News and Features
Doncha just love Side Channel Attacks? This time it is a successful timing attack, grabbing ‘secret’ keys from RSA and DSA cryptography. There are similar attacks against AES-256 in case you were thinking of gloating.
Successful timing attacks on elliptic curve cryptography – The H Security: News and Features
9 May – There are a number of odd exploits out there that we should all be aware of, For example, Mac users of Skype should make certain that they are running Version 5.1.0.922 since there is a bizarre hole in previous versions that allow a clever person or worm to contact the user and then create a shell that can take over the Mac. See: Confusion over Skype for Mac security issue – H Security
For users of the Check Point Router and VPN/SSL client, there is also an exploit in the previous versions of software. Get the latest. See: Security update for Check Point for SSL-VPN clients – H Security
Finally, Google Images are being loaded with worms and trojans. Instruct your employees and friends to stay away…don’t send pictures, don’t send links until Google solves this. Both Krebs on Security and H-Security have explanations of this problem.
Scammers Swap Google Images for Malware — Krebs on Security
Google Images search results may lead to malicious sites – The H Security
28 April – The Coreflood botnet gets an effective smack from Microsoft. If you are using MS software, be certain to do a software update now. Usually MS only updates on the 2nd Tuesday of the month but the Coreflood villains have learned to take advantage of this with the millions of computers that it has infected.
Read the H-Security article for more solutions to this mess. You’ll thank yourself and MS too: Microsoft releases out-of-schedule update for anti-malware tool – The H Security: News and Features
21 April – Relief; Reader and Acrobat Patched – Update Now. This is a ActiveThreat™ Alert.
Krebs on Security: Adobe Reader, Acrobat Update Nixes Zero Day — Krebs on Security
16 April – Again with the UPDATE NOW!! This time only Flash because Adobe can’t keep up and won’t have the Reader updates available for at least a week. But the ActiveTricksters™ aren’t waiting. Read about it at Krebs On Security – Time to Patch Your Flash
22 Mar – Update NOW!! Flash and Reader Repaired – Get the links and story from Krebs: Critical Security Updates for Adobe Acrobat, Flash, Reader — Krebs on Security
15 Mar – Ouch! A new and in the wild Flash and Reader security problem won’t have a fix until 21 March. Krebs reports the whole story here:
Adobe: Attacks on Flash Player Flaw — Krebs on Security
“Adobe warned today attackers are exploiting a previously unknown security flaw in all supported versions of its Flash Player software. The company said the same vulnerability exists in Adobe Reader and Acrobat, but that it hasn’t yet seen attacks targeting the flaw in those programs.
In an advisory released today, Adobe said malicious hackers were exploiting a critical security hole in Flash (up to and including the latest version of Flash. The software maker warned the vulnerability also exists in Adobe Flash player 10.2.152.33 and earlier versions for Windows, Mac, Linux and Solaris operating systems (10.2.154.13 and earlier for Chrome users), Flash Player 101.106.16 and earlier for Android. In addition, Adobe believes the bug lives in the “authplay.dll” component that ships with Adobe Reader and Acrobat X (10.0.1) and earlier 10.x and 9.x versions for Windows and Mac systems.”
9 Mar – New Java for Macs, a load of updates for Windows…
The turnaround for Java updates for Mac is very quick this time, and that’s good news. There was a lot of security problems in the last release from Oracle. Java Update 4 is available with the standard Update tool. You can read about the update here: About the security content of Java for Mac OS X 10.6 Update 4
Window Patch Tuesday also has critical updates, but that is usual and ‘do it now’ necessary.
Also ‘do it now’ necessary is a critical Shockwave update patch, and an Adobe Flash update available here.
As Krebs On Security points out, you must update for each browser that you have on your computer. Check whether you have the latest version at this page.
Krebs also points out that Apple has a new iTunes for Windows that has dozens of security fixes. Use the new Windows version of Apple Software Update that comes bundled with the iTunes. Why you have iTunes on your production computer that touches security keys is a different question. Rethink your security policies and always think Vigilance.
Patch Tuesday, Etc. — Krebs on Security
6 Mar – Check your Firefox Update. Two in the last few days. The latest is just a Java problem fix, but the last one and the one before that had more RED alerts to paint a stop sign. Security Advisories for Firefox 3.6
24 Feb – Microsoft’s virus scanner causes security problem – The H Security: News and Features
Read the report.
This brings up: Why do we pay attention to Windows news when most all the servers out there are Linux based?
The answer comes from two directions. First, It is a rare facility in any part of the distribution chain that doesn’t have Windows machines as part of their production cycle. Emails are sent and received with Windows, keys are downloaded from windows, pdf files are downloaded from windows, which are put onto USB sticks. These USB sticks are put into systems that are dedicated to creating terrific movies – but they aren’t set up to be updated against the latest virus or trojan threat.
Viruses and Trojans can be designed to bounce around, doing nothing to intermediate systems, staying dormant until they reach the target machine. The code that they are made of doesn’t register as a virus by the transmitting machines, meaning that your desk computer won’t alert you if the pdf you put on your USB stick has a Linux virus.
In truth, it seems like a stretch to assume that someone would write a program for some target machine that requires several dozen steps before it is able to wreck havoc. But tell that to the Iranian Nuclear Facility. Tell that to the US Dept. of Defense, whose systems took two years to clear from a virus caught by a USB stick from a laptop of an employee.
DCinema systems are under the radar now. The movies on them are very secure. Only 11 of the 16 layers of AES-256 encryption have been broken. It is easier to pirate movies off the screen.
Which brings up the 2nd viewpoint: Proper security is done by design, not by luck.The habit of constant vigilance takes a long time to build.
Enough said.
23 Feb – H-Security reports “As expected, Microsoft has made the first Service Pack for Windows 7 and Server 2008 R2 available for download and started to distribute it via Windows Update.” For links and ideas, go to the original article:
Service Pack 1 for Windows 7 available for download – The H Security: News and Features
17 Feb – Limit the exploitability of the SMB flaw by blocking the BROWSER protocol at the network edge.
New SMB Bug Found in All Versions of Windows.
Yeah; that’s all you need to do. Read: Notes on exploitability of the recent Windows BROWSER protocol issue – Security Research & Defense – Site Home – TechNet Blogs
16 Feb – Oracle Updates Java for 21 Vulnerabilities – www.esecurityplanet.com – Mac users have to wait until Apple makes a change in their update code. This took weeks last time.
10 Feb – GMail gets high tech password option – Advice: Use it.
Details at KrebsOnSecurity: Google Adds 1-Time Passwords to Gmail, Apps
More data on One Time Passwords:
Intel Introduces One Time Password Hardware)
Symantec Introduces Game Changer for Strong Authentication Credentials
Intel, Symantec and Vasco propagate single-use passwords – The H Security: News and Features
8 Feb – Adobe, Microsoft Patch Tuesday; 29 Security problems with Adobe, 22 from Microsoft, 5 of which are “Critical”. There are reports of problems with the updates. Changes to the OS behavior are reported as well. Time to change to Reader X if you haven’t already done so. It seems a lot better in terms sandboxing problems: Adobe Reader X Update
Read Krebs on Security:
Adobe, Microsoft, WordPress Issue Security Fixes
31 Jan – H-Security provides an important update to the 27 Jan story from Krebs below. “Apparently Trusted Websites” is what catches my eye, and a reference to a blog post that shows how to test for vulnerability. See:
Microsoft warns of cross-site scripting in Windows – The H Security: News and Features
27 Jan – “Hackers have published instructions…” Words that have to make Microsoft quiver. Do you go to sites that need to handle MHTML? All versions of Windows are exposed to the siphoning of user data, or worse.
Firefox has an MHTML add-on, which most people wouldn’t know to download, unless you need to open web archives from Windows users. This happened to your editor just last week. turn off this Firefox add-on.
Microsoft: Exploit Published for Windows Flaw — Krebs on Security
12 Jan – Microsoft confirms what ITPro reports, that the Internet Explorer bug is in the wild now. It points out that the latest updates will close the hole created (but still leaves the Zero-Day unprotected.) Warning: Don’t have unprotected IE internet.
Microsoft warns IE flaw is being exploited | IT PRO
11 Jan – Microsoft Plugs 3 Security Holes, 1 Critical. Zero-Day flaws go unfixed. Update now anyway. Story well told at: Microsoft Plugs Three Windows Security Holes — Krebs on Security, which notes: Microsoft has released two separate FixIt tools to help users mitigate the threat from a couple of the more pressing outstanding vulnerabilities. If you use Windows, and especially if you browse the Web with Internet Explorer, you should take a moment to take advantage of these stopgap fixes, available here and here.
6 Jan – Mac OS 10.6.6 released; among the 126Mb download is one security fix, having to do with an obscure man-in-the-middle attack. Most of the update seems to be interfacing the AppStore, except for a couple odd issues with the mouse pointer and cropping postscript. Doesn’t seem essential unless they are hiding something. But, it worked with no problems on my old MBP.
Mac OS X v10.6.6 Update Combo
Mac OS X v10.6.6 Update
4 Jan – Imagine that…Microsoft starts the New Decade in a panic. Krebs on Security reports Microsoft Warns of Image Problem — a disappointing set of circumstances brought notice to this Graphics Engine bug because a Google spider broadcast it before Microsoft found a solution to this XP, 2003 Server and Vista security hole.
Microsoft’s solution – escalate access rights in such a way that thumbnail pictures are no longer displayed…ever. You can do that either with chaning shimgvw.dll library or buying a Mac.
IT Pro reports: “With Patch Tuesday due next week, Microsoft may fix numerous issues, including a flaw affecting all versions of Internet Explorer. Microsoft investigates Windows zero-day flaw | IT PRO
“Hackers could have take advantage of the security hole through a technique which lets attackers get around two important security defences in Windows 7 and Vista.
“Meanwhile, a Google researcher has warned details on a potentially serious vulnerability affecting the Microsoft browser could be in the hands of Chinese hackers.”
23 Dec – I can’t imagine anyone clever enough to read this is un-clever enough to us Internet Explorer. But, if someone you know is, read them this from H-Security: Microsoft issues warning about critical IE hole – An exploit recently went into circulation for a critical security flaw in Internet Explorer (IE), so you could infect your computer if you visit a specially crafted malicious website. In an advisory, Microsoft warns of the danger, confirming reports claiming that Internet Explorer versions 6 to 8 are vulnerable in all Windows editions.
14 Dec – 40 Security holes patched in 17 updates including STUX and other ‘in the wild’ vulnerabilities. URGENTLY – Get them all now through Windows Update.
Then, rush over to How to opt-out of Microsoft Spynet – Disable Microsoft Spynet | Malware Help. Org – The theory is that Microsoft has shown that they can’t be trusted to safely operate a spynet on your computer, even if it was a good idea…which it ain’t.
10 Dec – Windows Users – Wake up on the 14th to finally getting an update to fix the Stux and other problem areas. Then rejoice.
9 Dec – Mac users still using Microsoft Office – Microsoft Office 2008 for Mac 12.2.8 Update; something about “potentially be exploited to poison the proxy cache and inject manipulated pages.”
December – 16 vulnerabilities fixed in QuickTime, both for Mac and PC, immediate upgrade advisable, though these are fixed if you are upgraded to 10.6.5. About the security content of QuickTime 7.6.9
Windows download site.
H-Security has an article that shows how Linux root privileges are not secure: OOPS – Root privileges under Linux
New version of OpenSSL fixes two vulnerabilities including Password Authenticated Key Exchange by Juggling” protocol (J-PAKE) allows intruders to authenticate themselves without a secret key.
Are you using WordPress with remote publishing turned on? Now is the time to update. – WordPress 3.0.3 security update released
Don’t mess with the beta Firefox 4 v7 – Version 8 has removed transparent proxies whichcan potentially be exploited to poison the proxy cache and inject manipulated pages.
22 Nov – Don’t read the Security Notes for IOS 4.2: About the security content of iOS 4.2
Just set aside 75 minutes or so, and do the auto update. Don’t click on anything, especially while it is syncing. Worked for me…even kept my ‘folders’.
Read some of the other articles at DCinemaTools instead. Or, write your own and submit.
19 Nov – Side note; Interesting use of cloud based GPU power to crack passwords. See:
GPUs crack passwords in the cloud. Harbinger Alert. Get a stronger password security plan.
19 Nov – Apple Safari incorporates 27 security Critical Updates in the open source WebKit engine. Don’t delay. Use your auto-update feature in Safari immediately. It will require a reboot of the computer.
16 Nov – Critical vulnerabilities have been identified in Adobe Reader 9.4 (and earlier versions) for Windows, Macintosh and UNIX; so begins the Security Bulletin for Adobe Reader 9.4.1. The current updated Adobe Security Advisory for Flash and Reader reminds us to check that we have Flash Player 10.1.95.2, which is weird since I have version 10.1.102.64 – Check your version of Flash here, or at the permanent link on the DCinemaTools.com Front Page.
Reader Download Center
Adobe Flash Player Download Center
Krebs In Security makes the following points:
Note that this is not the sandboxed version (Adobe Reader X, or v 10.0) which is expected to be released at the end of this month.
Separately, the company is warning users not to fall for recent phishing and other e-mail scams targeted at Adobe customers looking for the Adobe Acrobat X, a new product being released this week. “Many of these emails require recipients to register and/or provide personal information. Please be aware that these emails have not been sent by Adobe or on Adobe’s behalf,” Adobe said.
11 Nov – 10.6.5 OSX Upgrade with over 50 Security Fixes. Dozens of them appear to be for the Flash Plug-in…
About the security content of Mac OS X v10.6.5 and Security Update 2010-007
I just used the standard Software Upgrade without problems, but it is also possible to download the Combo Update:
Mac OS X v10.6.5 Update (Combo)
November – The new Flash Player should be installed. Who needs 18 security holes (since the last release). Of course, a newly discovered hole in the authplay.dll wasn’t patched, but really, who uses PDFs with multimedia anyway.
Flash Player 10.1.102.64 is available to download for Windows, Linux and Mac OS.
For more see H-Security: Adobe: hole closed, hole open
27 October: URGENT – STOP Using Firefox…Now! Until you read this and install script-blocking add-on like NoScript. Read this piece at Krebs on Security: Nobel Peace Prize Site Serves Firefox 0day. Update…It appears to only attack Windows XP, but that is not for certain.
19 October: Apple Mac Java Update: Amazing 1 week turnaround for an Apple Java Update. Use your standard Apple Update pulldown; many security vulnerability fixes. Very important.
Java for Mac OS X 10.6 Update 3
Java for Mac OS X 10.5 Update 8
20 October; RealPlayer is in the news with a new version that fixes seven critical vulnerabilities that they admit to, and remember, vulnerability means that they could be used to compromise host systems (that’s your computer) remotely if left unpatched.
Firefox fixes and Java passes Adobe in security exploits. (Clue – Exploits mean attacked and found attackable.)
According to Java surpasses Adobe kit as most attacked software • The Register,
Oracle’s Java framework has surpassed Adobe applications as the most attacked software package, according to a Microsoft researcher who warned she was seeing “an unprecedented wave of Java exploitation.”
Hmmm. A Microsoft spokesperson assailing Java and Oracle in one paragraph. This author apologizes for wasting your time. We’ll get less biased sources next time.
Meanwhile, Firefox’s 3.6.11 fixes several flaws that hackers have been using, so if your DCP passwords are coming off a system that is also using Firefox, upgrade now. Performance and stability are also improved. Mozilla Firefox 3.6.11 Release Notes
12 October – Who is comfortable seeing the Oracle name when you see the word Java? Notwithstanding, 30 bug and security fixes – The official Java Download page. Not for Macs…they usually follow a while after, but the last MacJava update took care of a critical problem a month ago that is only now being fixed for everyone else.
5 October – After a long period (about 6 weeks) without a bug and security fix, Adobe releases new versions of Reader and Acrobat with the nuanced reason of “…a Flash player update as well as numerous bug fixes. Several security fixes are included as described here and here. The operative language is: “Critical vulnerabilities have been identified in Adobe Reader 9.3.4 (and earlier versions) for Windows, Macintosh and UNIX, Adobe Acrobat 9.3.4 (and earlier versions) … could cause the application to crash and could potentially allow an attacker to take control of the affected system. Adobe recommends users of Adobe Reader 9.3.4 and earlier versions for Windows, Macintosh and UNIX update to Adobe Reader 9.4. …”
Since I get 3 or 4 crashes a week with my Flash plug-in for Safari and don’t use Reader at all, this isn’t so critical to me. But I see dcinema players, and computers where people manipulate their keys, with different versions of Reader – none of them are what Adobe calls secure…well, they call them secure when released, but weeks later they change their minds.
9 September–Continued UltraCritical–Can bypass Windows 7 and Vista Protection–Bottom Line…start using PDF/A format in-house–Adobe warns of zero day vulnerability in Reader and Acrobat
Opera DLL vulnerability fix–Read: Opera 10.6 update addresses DLL vulnerability
Adobe warns of zero day vulnerability in Reader and Acrobat – The H Security: News and Features
iOS 4.1 released for iPhone and iPod touch – I’ll let you know if it helps my battery drain, but there are also 24 critical security fixes.
8 September–Mozilla fixes Firefox holes, curtails clickjacking. Go to this link for all details:
Mozilla fixes Firefox holes, curtails clickjacking | Deep Tech – CNET News
7 September–Get on top of Safari Updates…more security…run Software Update now.
26 Aug–DLL scare continues. Many more programs found vulnerable. Double check you firewall. Then read this article in H Security: Scope of DLL security problem widens – Update
25 August–Shocking Shockwave | 18 Critical vulnerabilities
Here is the download link.
24 August–Apple OS again….Security this says.
19 August–Adobe again. Reader. Out of Cycle Security Patch.
13 August–The Adobe Flash update reported yesterday for the Mac version 10.1.82.76 is joined with other versions as a mandatory security update that covers many security problems. H Security reports the details. ITPro also examines some specifics.
In positive news, reports that Macs were vulnerable to the Eleonore online banking trojan have proved to be false.
Apple did patch Quicktime for Windows. Mandatory Security Update…though not for Macs.
12 August–iOS 4.0.2 update for the iPhone (and iPod touch) and iOS 3.2.2 Update for iPad were released today to fix security flaws that allow PDF files to contain “maliciously crafted embedded fonts may allow arbitrary code execution.” Get down. The links above go to the Security Description pages on Apple’s website.
DO THIS UPDATE NOW. Depending on the cycle that you have set, you may not be notified of this update for a week or more. Crafty PDF coding is becoming rampant. Corporate solution: Encode your PDF files with version A, which can’t contain motion pictures and other un-needed things.
Adobe is also in the news with a new Flash for the Mac (This link goes to Adobe’s Tech PR). Your editor became a guinea pig this morning. The old MacBook Pro still works, if that means anything to you. Download site is here. The version as of this morning was 10.1.82.76
DO THIS UPDATE NOW (ALSO) – It not only fixes security holes, but speed is improved:
“In internal testing, we’ve seen dramatic performance improvements — up to two-thirds reduction in CPU utilisation for 1080p H.264 video playback”, but it also has Security enhancements. Yes. I know. What a surprise. You did get your Adobe Reader updates…oh, not ready yet? Sorry. Beware. There are problems in the wild.
10 August: Microsoft: 14 bulletins to address 34 vulnerabilities
Adobe: Not posted yet, but upgrades to Reader and Acrobat promised today
5 August–Microsoft will have a fix for a critical zero-day hole in all supported versions of Windows which is already being exploited…supposedly on Monday, 9 August.
See the eSecurity Planet story at: Out-of-band Microsoft Security Patch Coming Monday
29 July – Big App Upgrade Time
Firefox, Safari, Adobe Reader and Flash all have new upgrades that are required for security reasons. Put a couple hours of your weekend aside for back-ups and upgrades!
If you didn’t do Open Office to 3.2.1, better get that too.
25 June – Look for an important set of releases for all platforms which use Adobe Reader. Adobe brings forward security update for Reader
Whether you need or don’t need the functionality, Upgrade to the latest Apple everything; Safari 5, 10.6.4, Quicktime, Java…there are too many major repaired security holes to count and comment upon.
7 June – OpenOffice brings 2 security reports on the new version 3.2 (fixed with 3.2.1), including SSL/TLS and Python problems. Don’t delay.
5 June 2010 – Yet again, Adobe Flash, Reader and Acrobat is in the vulnerability news. H Security reports:
According to a security advisory from Adobe, there is a critical vulnerability in Flash Player 10.0.45.2 (and earlier versions) and in the authplay.dll component that ships with Adobe Reader and Acrobat 9.0; Windows, Mac OS X, Unix and Linux versions are all vulnerable. Attackers can exploit the hole to crash the software or gain control of the system and there are already reports of exploitation in the wild for all three products.
The Flash Player 10.1 release candidate is apparently not vulnerable and Adobe offer the option of installing this as a mitigation step. For Reader and Acrobat 9.x, Adobe recommend deleting, renaming or removing access to theauthplay.dll file to mitigate the threat. On Windows, this file is typically located at C:\Program Files\Adobe\Reader 9.0\Reader\authplay.dll for Adobe Reader or C:\Program Files\Adobe\Acrobat 9.0\Acrobat\authplay.dll for Acrobat. Adobe say that Reader and Acrobat 8.x are not vulnerable.
2 Jun 2010 – Finally, a Mac serious malware problem in the field. It ain’t a virus or a worm (though it can self-update), but it does send data and open a back door. Martin James, at IT Pro Security reports:
Security firm Intego has warned Mac OS X users that downloading free software from several popular download sites may install spyware that opens a back door for hackers to collect personal details.
The spyware, called OSX/OpinionSpy, is a variant of a Windows threat first discovered in 2008. It has been found piggy-backing on nearly 30 screensaver downloads from a company called 7art and a video converter app called MishInc FLV to MP3.
Softpedia, MacUpdate and VersionTracker were all found to be hosting the infected downloads, which have now been withdrawn, Intego said.
Read the entire report. Your family members will be calling you.
Spyware found on popular Mac websites
27 May—IT Pro Reports potential intercept vulnerability in Cisco’s Network Building Mediator products.
Cisco warns that there are numerous vulnerabilities that could lead to malicious parties taking complete control over affected devices. The NBM units are used in professional installations to monitor a building’s operations with IT; the status of doors, energy consuming devices, and overall efficiency.
Importantly, it is tied to the IT network where certain security gaps allow unauthorised users to change a device’s configuration.
“A malicious user must authenticate as an existing user but does not need to have administrator privileges or know administrator credentials to modify device configuration,” the company noted.
Other vulnerabilities mean that interactions between an operator workstation and the Cisco Network Building Mediator could be intercepted by any willing person.
“A malicious user able to intercept the sessions could learn any credentials used during intercepted sessions (for administrators and non-administrators alike) and could subsequently take full control of the device,” Cisco explained.
Other threats include potential password theft and account data loss.
As usual, whether you have the particular devices listed below, it is critical that your DCinema system stays secure, so awareness of all devices in the room is critical.
The weaknesses affect the legacy Richards-Zeta Mediator 2500 product and Cisco Network Building Mediator NBM-2400 and NBM-4800 models as well as Mediator Framework software releases prior to 3.1.1.
Given that the “workarounds” offered by Cisco are somewhat limited, affected firms will want to get hold of the free software updates that the provider has issued to deal with the security holes.
24 May—
IT Pro Security reports that IBM has distributed USB sticks at a conference in Australia this week which were riddled with malware – two separate worms to be exact – and the company was forced to send out emails to the recipients warning them and asking them to return the sticks to IBM’s Australian headquarters as soon as possible.
So, raise your hands if you ever used a give-away USB stick on your computer.
Again, the message; Constant Alertness. One clever trojan that can send log files outbound, or a pdf with a worm that can spread though a network and attach itself to media files, and the game gets too interesting.
14 April—Microsoft, Adobe and Oracle have all issued important security updates as part of this month’s Patch Tuesday. ITPro for Business
Microsoft has issued 11 patches to fix 25 flaws across Windows, Office and Exchange as part of its monthly update cycle.
Of the 11 patches, five were rated critical, five were important, and the last was moderate.
Microsoft highlighted three – MS10-019, MS10-026, and MS10-027 – as being priorities for administrators. The first affects all versions of Windows and allows for code to be executed, while the latter pair could be triggered just by visiting a malicious web page.
Microsoft’s security communications manager Jerry Bryant also warned that one of the patches is a Windows Kernel update, and therefore includes a system to check for rootkits, after the last kernel update uncovered a few infections.
8 April 2010—PDF virus spreads without exploiting any flaw
A security researcher has demonstrated a proof-of-concept attack that could allow malicious PDF files to spread to other PDF files on a system without exploiting a specific vulnerability.
Jeremy Conway, a product manager at NitroSecurity, built on the work done by fellow security specialist Didier Stevens to come up with an attack that could spread malicious code into clean PDFs as part of an incremental update.
Last week, Stevens showed how a program launch action triggered by the opening of a PDF could be exploited to execute code embedded in the PDF. Stevens also demonstrated that the pop-up dialogue box normally accompanying such a launch action could be partially manipulated to give users a false sense of security.
However, Conway – who says he was inspired by Stevens’ work – said the vulnerability could be used to infect other PDF files with the same problem.
17 Fevrier–Acrobat and Reader users are strongly encouraged to install an update that fixes ‘critical security holes’. ScanSafe reports that 80% of web-based exploits attacked Adobe Reader vulnerabilities.
Updates links for Windows, Mac and Linux 9.3.1 version of Reader.
Firefox has also released their 3.6 version – much enhance security and speed.
Krebs on Security also reports:
If you decide to do without Adobe Reader and uninstall it, you might want to nix the Adobe Download Manager as well. Researcher Aviv Raff points to some nifty work he’s done which shows that Adobe’s Download Manager — which ships with all new versions of Flash and Reader — can be forced to reinstall an application that’s been removed, such as Reader.
According to Raff, a Web site could hijack the Adobe Download manager to download and install any of the following:
Adobe Flash 10
- Adobe Reader 9.3
- Adobe Reader 8.2
- Adobe Air 1.5.3
- ARH tool – allows silent installation of Adobe Air applications
- Google Toolbar 6.3
- McAfee Security Scan Plus
- New York Times Reader (via Adobe Air)
- Fanbase (via Adobe Air)
- Acrobat.com desktop shortcut
Raff writes: “So, even if you use an alternative PDF reader, an attacker can force you to download and install Adobe Reader, and then exploit the (yet to be patched, but now known) vulnerability. The attacker can also exploit 0-day vulnerabilities in any of the other products mentioned above.” Read more on his findings atthis link here.
Acrobat update Links
10 February
Along with 13 update bundles and a critical rating for this months exploit vulnerability patches, Microsoft is stealing the Nike slogan, saying “Just freakin’ do it” – change your operating system, change anything that came with it (Paint, anyone?), especially that Internet Explorer dated from 6 years ago…and XP too while you are at it.
And, if you get a Bluescreen after updating, check this post at Krebs On Security
Oy!
February 4–The iPhone gets an update…just plug it into iTunes and get OS 3.1.3 – and Apple gets FUD from InformationWeek.
20 Jan, 2010–In a wave of ‘finally’, Apple and Shockwave get much needed security upgrades. For Apple, use the update utility, or go to Apple-Support-Downloads; they have also finally caught up with the Windows 7 upgrade for Bootcamp.
Shockwave is a bit heavier, and applies to both PCs and Macs. It requires a manual uninstall, a reboot, an install, and another reboot. But, it is supposed to fill the glaring hole that has been present (and exploited) security risk: The patches fix multiple integer overflow and buffer overflow flaws that can be exploited to execute malicious code on computers that use the software.
Get your Shockwave 11.5.2.602 here.
This is the Friday, 15 Jan Report
Finally—Adobe Reader is safe. Well, at least it no longer has the hole that was allowing people in for the last few months. Update Now. Read no more. This is all for now. Even Firefox is playing nice.
December Firefox 3.5.6 handles 3 critial security issues – great strides from the two previous releases. There were 62 bug fixes. Seems like a lot of work for handling a version that will be superceded in the next few months, but 3.6 is still in alpha. (We have been informed that 3.0 is losing support as of Jan 2010.)
Meanwhile, Adobe can only be described as refusing to fix the zero-day trojan that has active exploits, until January 12. This strikes Windows systems at the current software rev, 9.2 and below…since anything below passed other problems like a sieve, this is not a good solution.
Hire someone to check your virus protection on a regular basis if you are using Windows.
See articles at CNET Security; Firefox 3.5.6 patches and Adobe to patch zero-day Reader, Acrobat hole [BFD-Editor] – Note the part where Adobe says that they’d rather not spend the extra time and money over the holidays to fix this hole.
This weekend is a great one for setting aside whatever time it takes to back up everything and then replace each program that you use with the latest version.
Looking at the security notes for this weeks releases of Safari, and Firefox, Adobe Shockwave and the recent Reader upgrades are downright scary. The Operating Systems changes were also important.
Cute little terms like ‘unexpected application termination or arbitrary code execution” and “maliciously crafted website may lead to the disclosure of local information.” A less subtle writer might put exclamation points after a big “WTF?’
Don’t waste time reading any more of this note than you must.
1) Buy whatever backup disk you need
2) Back up Now!
3) Open every program that you use. Check for an update.
4) Then, when your updates are finished…Back up again.
That is all. Go. Now. Please. I don’t want to read your complaints about arbitrary code disclosing your local information.


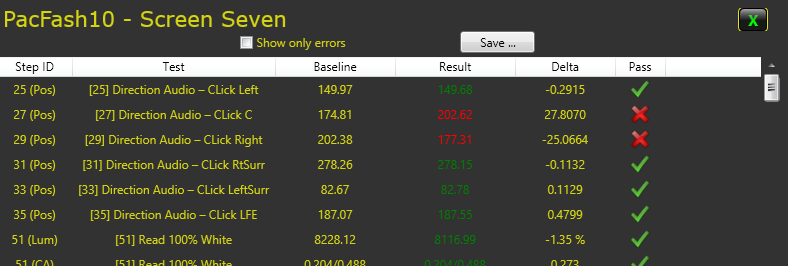 Swapped Inputs in Red, with Baseline and Results in degrees on the polar coordinate system, and the change from the baseline shown in degrees from the baseline’s reading.
Swapped Inputs in Red, with Baseline and Results in degrees on the polar coordinate system, and the change from the baseline shown in degrees from the baseline’s reading.