OK, so it is some fancy pants place that can’t spell the word Center properly. And, it is too late to get the promised artwork. Big deal. Enjoy the download and give a little.
Category Archives: Autre Intérêts
It is a big world out there.
Good Lessons on Violence Response
Weekend Time Sponges
Pixar: Where Steve Jobs’ Greatest Gifts Live On
BSPR – Ultimate Acronym or Cloud Guarantee?
We bring it up because we like the idea of someone certifying their safety, and taking responsibility for it. There must be some ‘out’, since hithertoo unknown flaws seem to take precidence over following all the compliance rules. But it is nice that the EU might put this in place, which will make it harder for cloud providers, yet by leveling the playing field toward quality it will make the whole system shine.
From the artilce:
When the EU drafts a new data protection law in November, it will introduce rules designed to ensure cloud providers are offering a safe service, IT Pro has learned.
The Binding Safe Processor Rules (BSPR) will ask cloud service providers working in the EU to agree to becoming legally liable should any data offences occur at their data centres, lawyers said yesterday.
It will effectively act as an accreditation scheme for cloud providers, meaning it will need vendors to sign up to the initiative.
However, the driving force behind the new rules, partner at Field Fisher Waterhouse Eduardo Ustaran, said service providers were certain to sign up as it would give them a much-needed selling point and, if they didn’t, they would be seen as unsafe to use.
To get that accreditation, vendors would have to prove their security models were adequate as well, Ustaran said.
“Cloud service providers would be given an accreditation from their data protection authority,” Ustaran told IT Pro.
Verizon Business is one organisation that has been pushing for the EU to enshrine the BSPR concept in data protection law, which is now set to happen.
Stewart Room, partner in FFW’s Privacy and Information Law Group, described it as the “bridge” for cloud adoption, given the fears around being legally liable if data offences occur in the cloud.
However, it will do little to allay fears around the US Patriot Act, which is fast emerging as a real threat to cloud adoption. The law effectively means the US can search through any US-run cloud provider’s data centres to find information on illegal activities.
For companies planning on using vendors with data centres in the US, this poses a significant obstacle to cloud adoption.
The European Parliament has already raised concerns about the impact of the Patriot Act and its effective overriding of EU data protection laws.
Legal changes incoming
In November, the EU will publish the draft new data protection law, which will form the basis of national legislations for the next 15-20 years. This will replace the current Data Protection Directive and the Data Protection Act in the UK.
Outside of the new Binding Safe Processor Rules, mandatory breach disclosure will be embedded in the draft law.
“We are certain that mandatory breach disclosure laws will be contained with the new EU data protection law. The European Commission has made this clear already,” Room said.
This means companies will be required to report any breaches, making more work for Information Commissioner’s Office (ICO). It makes it much more likely private companies will be reprimanded by the watchdog, if it decides to show its teeth.
Room believes the ICO will order companies to provide records of any breaches on a monthly basis.
For further coverage of cloud computing visit our sister siteCloud Pro.
Women in STEM: A Gender Gap to Innovation
• Although women fill close to half of all jobs in the U.S. economy, they hold less than 25 percent of STEM jobs. This has been the case throughout the past decade, even as college-educated women have increased their share of the overall workforce.
• Women with STEM jobs earned 33 percent more than comparable women in non-STEM jobs – considerably higher than the STEM premium for men. As a result, the gender wage gap is smaller in STEM jobs than in non-STEM jobs.
• Women hold a disproportionately low share of STEM undergraduate degrees, particularly in engineering.
• Women with a STEM degree are less likely than their male counterparts to work in a STEM occupation; they are more likely to work in education or healthcare.
There are many possible factors contributing to the discrepancy of women and men in STEM jobs, including: a lack of female role models, gender stereotyping, and less family-friendly flexibility in the STEM fields. Regardless of the causes, the findings of this report provide evidence of a need to encourage and support women in STEM.
A good synopsis is at: Study: Women Aren’t Taking Science And Tech Jobs | TPM Idea Lab
iPad Security & Network Management Tips
Excellent Security Articles for iPhone/iPad users:
iOpener – How safe is your iPhone data? – The H Security: News and Features
Three iPhone and iPad security tips – The H Security: News and Features
Excellent iPad/iPhone Network Management Article:
Manage heterogenous systems with your iPad | ITworld
Video to iPad/iPhone/Android Direct
The Vulkano Flow gives consumers the freedom to watch their TV anywhere in the world using smartphones, tablets and computers. Vulkano users can now instantly begin recording their favorite television programming so they never miss historic news or memorable sporting moments.
“The Vulkano line of devices has been created to offer consumers the ultimate flexibility in entertainment and we are proud to be the first to offer direct recording and DVR for mobile devices,” said Colin Stiles, EVP Sales and Marketing at Monsoon. “Consumers are making smartphones and tablets an essential part of their every day lives and are expecting to view and browse the TV content that they pay for at their leisure, no matter where they are in the world.”
Summary of Direct to Mobile Recording and DVR features on Vulkano Devices:
- Direct to mobile recording supports iPhone, iPad, and Android phones and tablets
- Full DVR capabilities including Pause, Rewind and Fast Forward
- iPhone/iPad recording in mp4 formats containing H264+AAC
- Android recording in mp4 formats containing H264+AAC
- iPhone/iPad recording in D1 or 640×480 or 352×240 resolutions
- Android recording in D1 or 640×480 or 352×240 resolutions
- Insufficient memory alert
Pricing and Availability
The Vulkano Flow ($99.99) is now available at Fry’s Electronics, Amazon, MicroCenter, other leading retailers and etailers as well as at www.myvulkano.com. Android, tablet and additional smartphone applications can be purchased for $12.99 each in their respective app stores.
About Monsoon Multimedia
Monsoon Multimedia provides advanced, standards-based multimedia products and convergence technologies for the PC, Mac, iPad and major smartphones. Founded by the founders of Dazzle and Emuzed, the company has offices in California,India, Russia and Singapore. For more information, please visit www.monsoonmultimedia.com.
Docu Makers Face Hobby Charge/Taxes
Educate > Money => Hobby = No Tax Write Off
US Tax Court Judge Diane Kroupa has decided that a documentary film maker is participating in a hobby, not a money making enterprise that doesn’t deserve tax write-offs for expenses. See: If You’re a Documentary Filmmaker, You Could Owe the IRS a Whole Lot of Money – indieWIRE
Photopic Sky Survey
 We deal in light, they deal in light. We’ve waited 15 years for d-cinema to mature. They’ve waited billions of years for dust to become sand and sand to become computers and computers to become cameras.
We deal in light, they deal in light. We’ve waited 15 years for d-cinema to mature. They’ve waited billions of years for dust to become sand and sand to become computers and computers to become cameras.
The site says: “The Photopic Sky Survey is a 5,000 megapixel photograph of the entire night sky stitched together from 37,440 exposures. Large in size and scope, it portrays a world far beyond the one beneath our feet and reveals our familiar Milky Way with unfamiliar clarity.” Take a break. Check it out: Photopic Sky Survey
Ohga-san Passes
Growing up in entertainment technology in the 70’s meant growing up with relationships with Sony in many areas of the business. The myth of the company revolved around two people; co-Founder Akio Morita and Ohga-san, Mr. Norio Ohga. (The other founder, Mr. Masaru Ibuka didn’t have as much of a public profile, for us gaijin at least.)
Your editor has had many incarnations of relationships with members of the Sony group, in Tokyo and Atsugi in Japan, in Los Angeles and New York and London. The spirit of the two pioneers most always seemed to have infused everyone with the desire for the highest quality in every aspect of the many games they played.
Ohga-san has passed. This article in the New York Times explains some of the attributes of the man: Norio Ohga, Who Led Sony Beyond Electronics, Dies at 81. May there be many more people like him.
PDF/A: Federal Court Requirement
The is a blog on the Adobe site, Acrobat for Legal Professionals, which has an article of interest:
Federal Courts Moving to Requiring PDF/A for Filings « Acrobat for Legal Professionals
It is interesting for the DCinema world because pdf files are regularly sent to projectionist’s computers which also have keys and critical private information on them. Even if company policy restricts non-cinema related material on a computer it would still be subject to the vagaries of chance that some pdf contained some version of malware. Unlike mail attachments, pdf files can have embedded files that don’t get caught at firewalls or by virus checkers.
And frankly, who has the time to keep up with all the updates that Adobe has thrown at us in the last two years?
Back to the article about the US Federal Court system not allowing any other version of pdf file except for PDF/A. They are not the first and won’t be the last to go this way. A lot of work went into making PDF/A an archival standard and many organizations mandate it. What is interesting is that it finally made it into the mainstream as lawyers file documents every hour and now have to learn how to create a PDF/A file correctly, constantly and easily.
In the article the author makes the following points about PDF/A
In a nutshell, here’s what you need to know about PDF/A:
- PDF/A is a specific flavor of PDF
- PDF 1.4 format (Acrobat 5 level file)
- All fonts embedded
- PDF/A is designed for long term archiving.
Files must be self-contained with no reliance on external players or links.
- PDF/A does not allow:
- Cross-document links (e.g. a link to a separate PDF file)
- Dynamic media such as movies or sounds
- Links to destinations outside the PDF itself including other PDFs and websites
- Security of any kind
- [Editor: Links can be made using standard HTML code.]
The entire article is worth reading. It is premised upon the user using Microsoft products, but it should be known that open source products like OpenOffice have an easy PDF/A creation tool, and Apple Macintosh products from Adobe also can follow this standard.
Eye better than camera capturing simultaneous contrast and faint detail
“One of the big success stories, and the first example of information processing by the nervous system, was the discovery that the nerve cells in the eye inhibit their neighbors, which allows the eye to accentuate edges,” said Richard Kramer, UC Berkeley professor of molecular and cell biology. “This is great if you only care about edges. But we also want to know about the insides of objects, especially in dim light.”
This terrific story comes from the terrific Terra Daily
Why the eye is better than a camera at capturing contrast and faint detail simultaneously
Kramer and former graduate student Skyler L. Jackman, now a post-doctoral fellow at Harvard University, discovered that while light-sensitive nerve cells in the retina inhibit dozens of their close neighbors, they also boost the response of the nearest one or two nerve cells.
That extra boost preserves the information in individual light detecting cells – the rods and cones – thereby retaining faint detail while accentuating edges, Kramer said. The rods and cones thus get both positive and negative feedback from their neighbors.
“By locally offsetting negative feedback, positive feedback boosts the photoreceptor signal while preserving contrast enhancement,” he said.
Jackman, Kramer and their colleagues at the University of Nebraska Medical Center in Omaha report their findings in the journal PLoS Biology. Kramer also will report the findings at the 2011 annual meeting of the Association for Research in Vision and Ophthalmology in Ft. Lauderdale, Fla.
Read the rest of the article at: Why the eye is better than a camera at capturing contrast and faint detail simultaneously
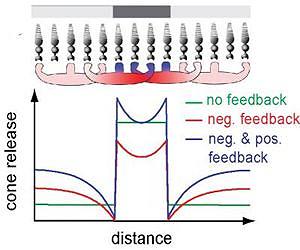 Cones normally release the neurotransmitter glutamate in the dark, while light decreases glutamate release. This graph of neurotransmitter release shows what happens when cone cells are exposed to a dark spot in a light background (top) under various scenarios, including no feedback (green trace) and only negative feedback from horizontal cells (red trace). Negative feedback to many cones enhances edges, but would decrease detail in dark areas were it not for newly discovered positive feedback that is localized to only a few cone cells (blue trace). Credit: Richard Kramer lab, UC Berkeley
Cones normally release the neurotransmitter glutamate in the dark, while light decreases glutamate release. This graph of neurotransmitter release shows what happens when cone cells are exposed to a dark spot in a light background (top) under various scenarios, including no feedback (green trace) and only negative feedback from horizontal cells (red trace). Negative feedback to many cones enhances edges, but would decrease detail in dark areas were it not for newly discovered positive feedback that is localized to only a few cone cells (blue trace). Credit: Richard Kramer lab, UC Berkeley
Fun Musician/Artist Site
A little fun work to get to the music…or maybe it will be different for you.
Stuxnet Solved
The worm then appears to have been introduced into Natanz via infected laptops or USB drives. There, Stuxnet infected the Siemens control systems and, specialists say, manipulated centrifugal speeds to a degree that caused permanent damage to the motors.
This article is derived from Stuxnet: five companies used as spring-boards – The H Security: News and Features which was taken from Symantics papers that can be seen here: Updated W32.Stuxnet Dossier is Available | Symantec Connect
It is interesting to the community because it shows that an attack on somewhat secure, but somewhat monoculture systems can be done. And since we have somewhat secure, but somewhat monoculture systems, it is a lesson toward the premise of being constantly vigilant.
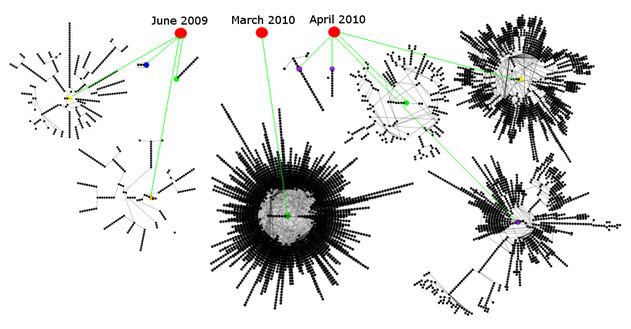
Symantec managed to trace the worm’s dissemination pathways and infection figures because Stuxnet itself apparently logs the computers it infects. The logged information contained exact timings and served as the basis for Symantec’s analyses. According to the AV vendor, 3,280 unique samples of the worm were responsible for approximately 12,000 infections.
Reportedly, the first attack took place in June 2009, and further attacks followed in July 2009, March 2010, April 2010 and May 2010. Various organisations were targeted repeatedly by the Stuxnet authors, and some computers were successfully infected several times.
The creators of the worm deployed three variants of Stuxnet via targeted attacks, but only the variant deployed in March contained what was a zero-day exploit for the LNK hole in Windows at that time. Using the timestamps in the compiled code, Symantec concluded that the first infection was already successful only 12 hours after the first version of Stuxnet was completed.
The new analyses show that Stuxnet actually contained two sabotage routines to infect and manipulate two separate types of control, but that the second routine was incomplete and disabled. Experts assume that the developers ran out of time.