The worm then appears to have been introduced into Natanz via infected laptops or USB drives. There, Stuxnet infected the Siemens control systems and, specialists say, manipulated centrifugal speeds to a degree that caused permanent damage to the motors.
This article is derived from Stuxnet: five companies used as spring-boards – The H Security: News and Features which was taken from Symantics papers that can be seen here: Updated W32.Stuxnet Dossier is Available | Symantec Connect
It is interesting to the community because it shows that an attack on somewhat secure, but somewhat monoculture systems can be done. And since we have somewhat secure, but somewhat monoculture systems, it is a lesson toward the premise of being constantly vigilant.
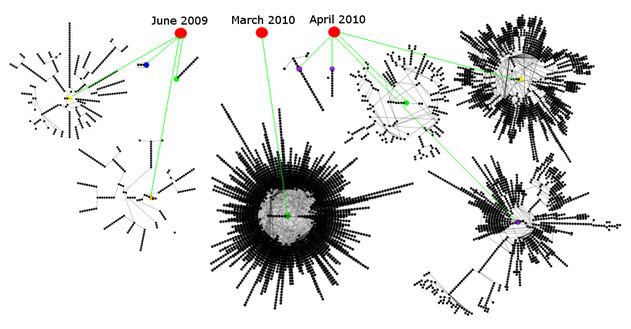
Symantec managed to trace the worm’s dissemination pathways and infection figures because Stuxnet itself apparently logs the computers it infects. The logged information contained exact timings and served as the basis for Symantec’s analyses. According to the AV vendor, 3,280 unique samples of the worm were responsible for approximately 12,000 infections.
Reportedly, the first attack took place in June 2009, and further attacks followed in July 2009, March 2010, April 2010 and May 2010. Various organisations were targeted repeatedly by the Stuxnet authors, and some computers were successfully infected several times.
The creators of the worm deployed three variants of Stuxnet via targeted attacks, but only the variant deployed in March contained what was a zero-day exploit for the LNK hole in Windows at that time. Using the timestamps in the compiled code, Symantec concluded that the first infection was already successful only 12 hours after the first version of Stuxnet was completed.
The new analyses show that Stuxnet actually contained two sabotage routines to infect and manipulate two separate types of control, but that the second routine was incomplete and disabled. Experts assume that the developers ran out of time.