This article is the beginnings of an article about SSL Certificates, what they look like, what they do, and what you should know so as not to be fooled.
The objective is pretty simple: To make it easy for the user’s computer to send and receive information from a site in a closed and secure environment.
Once a few steps are checked, the user can be assured that the data they are sending and receiving from the site is not going to be intercepted and mis-used. Most of the work is done by the “to be trusted” site, and one of a handful of 3rd party groups called Certificate Authorities (CA).
Now, in the digital cinema business the term certificate authorities comes up when speaking of the interchange of data between media server components and projector components. There are passwords (in the form of encrypted public and private keys) and encrypted data flying back and forth, and all refereed by CAs who follow rules set by a standards group or three.
The same is true in the web space, where keys are sent back and forth according to strict protocols. The user does’ t suspect any of this unless and until there is a gross problem. Usually the browser (Firefox, Safari, Chrome) notices certain clues that the sending site sends out, and if the browser doesn’t get more of what it needs for safe browsing it will either refuse to work or if it isn’t completely suspicious, it will tell the user the problem and ask the user for permission to continue.
Of course, absolutes don’t seem to exist…
SSL Certificate Explained – YouTube
{youtube}SJJmoDZ3il8{/youtube}
On the DCinemaCompliance.net demo site, there is a certificate from one of the major CAs named Comodo. They are major enough that Firefox and Chrome and Safari recognize them. If we got all our friends together to set up a certificate authority, we could do so but the browsers would throw up an error…probably each time. The user would have to grant authority.
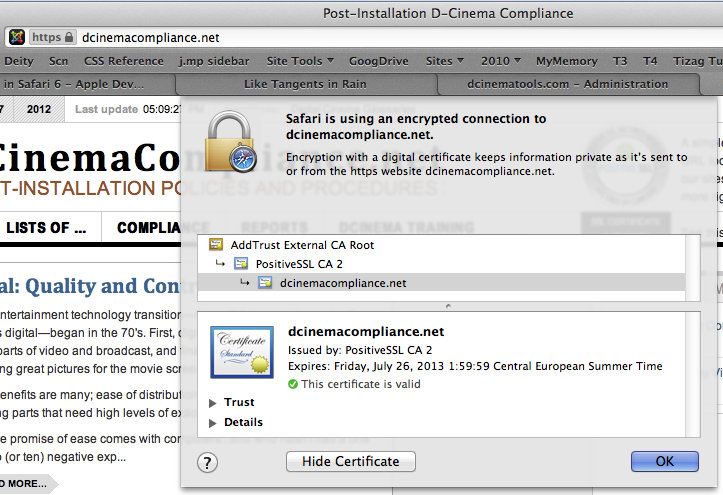
 The picture of a cert as on the DCinemaCompliance site might look cool and official, but it means nothing significant. It might remind you to look at the URL and see if it has one important feature: did the “http:” change to “https:”. A site that doesn’t have that ‘s’ wouldn’t be secure.
The picture of a cert as on the DCinemaCompliance site might look cool and official, but it means nothing significant. It might remind you to look at the URL and see if it has one important feature: did the “http:” change to “https:”. A site that doesn’t have that ‘s’ wouldn’t be secure.
![]()
You will notice that the URL is also colored green. It could also have a green or blue bar behind it, depending on which level of certificate was purchased from the CA. In this case the ‘s’ is showing so that indicates that a secure communication line has been created for the data to pass through. Without the bars behind it indicates that there is some material on the page that may not be completely secure, for example if there is a link to a non-secure site.
One should still be careful that there isn’t any of those famous key stroke stealing pieces of malware that can get whatever data you punch in. But that is the background of SSL.
The following two pictures show what happens when hitting the lock on a site with a valid certificate, and the identical site incorrectly using the same certificate…valid in one place and not another. Note that it will get goofy with questions if there is no means of qualification with a widely acknowledged certificate authority. There are private certs, but your browser will tell you and give you a chance to make your mind up about accepting them or not.
Part II will deal with how this is important to you as a user of the DCinema Compliance Post-Installation.